- Start a Meeting
| Join a Meeting
| Sign Up -
Welcome to https://Addammeting.com (the “Site”). We understand that privacy online is important to users of our Site, especially when conducting live video business. This statement governs our privacy policies with respect to those users of the Site (“Visitors”) who visit without transacting business and Visitors who register to transact business on the Site and make use of the various services offered by addameeting.com & telehealthy.us as cloud providers, & Doctors By Video, LLC. (collectively, “Services”) (“Authorized Customers”). “Personally Identifiable Information” Refers to any information that identifies or can be used to identify, contact, or locate the person to whom such information pertains, including, but not limited to, name, address, phone number, fax number, email address, financial profiles, social security number, and credit card information. Personally Identifiable Information does not include information that is collected anonymously (that is, without identification of the individual user) or demographic information not connected to an identified individual. What Personally Identifiable Information is collected? We may collect basic user profile information from all of our Visitors. We collect the following additional information from our Authorized Customers: the names, addresses, phone numbers and email addresses of Authorized Customers, the nature and size of the business, and the nature and size of the advertising inventory that the Authorized Customer intends to purchase or sell. What organizations are collecting the information? In addition to our direct collection of information, our third party service vendors (such as credit card companies, clearinghouses and banks) who may provide such services as credit, insurance, and escrow services may collect this information from our Visitors and Authorized Customers. We do not control how these third parties use such information, but we do ask them to disclose how they use personal information provided to them from Visitors and Authorized Customers. Some of these third parties may be intermediaries that act solely as links in the distribution chain, and do not store, retain, or use the information given to them. How does the Site use Personally Identifiable Information? We use Personally Identifiable Information to customize the Site, to make appropriate service offerings, and to fulfill buying and selling requests on the Site. We may email Visitors and Authorized Customers about research or purchase and selling opportunities on the Site or information related to the subject matter of the Site. We may also use Personally Identifiable Information to contact Visitors and Authorized Customers in response to specific inquiries, or to provide requested information. With whom may the information may be shared? Personally Identifiable Information about Authorized Customers may be shared with other Authorized Customers who wish to evaluate potential transactions with other Authorized Customers. We may share aggregated information about our Visitors, including the demographics of our Visitors and Authorized Customers, with our affiliated agencies and third party vendors. We also offer the opportunity to “opt out” of receiving information or being contacted by us or by any agency acting on our behalf. How is Personally Identifiable Information stored? Personally Identifiable Information collected by addameeting.com, telehealthy.us, and Doctors By Video, LLC. is securely stored and is not accessible to third parties or employees of Doctors By Video, LLC. except for use as indicated above. What choices are available to Visitors regarding collection, use and distribution of the information? Visitors and Authorized Customers may opt out of receiving unsolicited information from or being contacted by us and/or our vendors and affiliated agencies by responding to emails as instructed, or by contacting us Cookies A cookie is a string of information that a website stores on a visitor’s computer, and that the visitor’s browser provides to the website each time the visitor returns. Are Cookies Used on the Site? Cookies are used for a variety of reasons. We use Cookies to obtain information about the preferences of our Visitors and the services they select. We also use Cookies for security purposes to protect our Authorized Customers. For example, if an Authorized Customer is logged on and the site is unused for more than 10 minutes, we will automatically log the Authorized Customer off. Visitors who do not wish to have cookies placed on their computers should set their browsers to refuse cookies before using https://www.telehealthy.us and addameeting.com , with the drawback that certain features of website may not function properly without the aid of cookies. Cookies used by our service providers Our service providers use cookies and those cookies may be stored on your computer when you visit our website. You can find more details about which cookies are used in our cookies info page. How we use login information? We use login information, including, but not limited to, IP addresses, ISPs, and browser types, to analyze trends, administer the Site, track a user’s movement and use, and gather broad demographic information. What partners or service providers have access to Personally Identifiable Information from Visitors and/or Authorized Customers on the Site? Doctors By Video, LLC. has entered into and will continue to enter into partnerships and other affiliations with a number of vendors. Such vendors may have access to certain Personally Identifiable Information on a need to know basis for evaluating Authorized Customers for service eligibility. Our privacy policy does not cover their collection or use of this information. Disclosure of Personally Identifiable Information to comply with the law. We will disclose Personally Identifiable Information in order to comply with a court order or subpoena or a request from a law enforcement agency to release information. We will also disclose Personally Identifiable Information when reasonably necessary to protect the safety of our Visitors and Authorized Customers. How does the Site keep Personally Identifiable Information secure? All of our employees are familiar with our security policy and practices. The Personally Identifiable Information of our Visitors and Authorized Customers is only accessible to a limited number of qualified employees who are given a password in order to gain access to the information. We audit our security systems and processes on a regular basis. Sensitive information, such as credit card numbers or social security numbers, is protected by encryption protocols, in place to protect information sent over the Internet. While we take commercially reasonable measures to maintain a secure site, electronic communications and databases are subject to errors, tampering, and break-ins, and we cannot guarantee or warrant that such events will not take place and we will not be liable to Visitors or Authorized Customers for any such occurrences. How can Visitors correct any inaccuracies in Personally Identifiable Information? Visitors and Authorized Customers may contact us to update Personally Identifiable Information about them or to correct any inaccuracies by emailing us at [email protected] Can a Visitor delete or deactivate Personally Identifiable Information collected by the Site? We provide Visitors and Authorized Customers with a mechanism to delete/deactivate Personally Identifiable Information from the Site’s database by contacting. However, because of backups and records of deletions, it may be impossible to delete a Visitor’s entry without retaining some residual information. An individual who requests to have Personally Identifiable Information deactivated will have this information functionally deleted, and we will not sell, transfer, or use Personally Identifiable Information relating to that individual in any way moving forward. Your rights These are summarized rights that you have under data protection law The right to access The right to rectification The right to erasure The right to restrict processing The right to object to processing The right to data portability The right to complain to a supervisory authority The right to withdraw consent What happens if the Privacy Policy Changes? We will let our Visitors and Authorized Customers know about changes to our privacy policy by posting such changes on the Site. However, if we are changing our privacy policy in a manner that might cause disclosure of Personally Identifiable Information that a Visitor or Authorized Customer has previously requested not be disclosed, we will contact such Visitor or Authorized Customer to allow such Visitor or Authorized Customer to prevent such disclosure. Links: https://www.telehealthy.us and addameeting.com contains links to other websites. Please note that when you click on one of these links, you are moving to another website. We encourage you to read the privacy statements of these linked sites as their privacy policies may differ from ours.
HIPAA and Health IT
HIPAA is a federal law that protects the privacy of your personal health information. At the same time, it allows health care providers and certain related operations enough access to the information they need to do their jobs effectively. HIPAA includes several rules and provisions that set guidelines and requirements for the administration and enforcement of HIPAA.
The relevant ones for the implementation of health information technology and the exchange of protected health information in an electronic environment are the Privacy Rule and the Security Rule, as well as the HITECH Act which further enforced the two in 2009.
*State laws may have more stringent requirements than federal laws, however, in cases of conflict, federal
law supersedes state law.
Highlights Of The Privacy Rule, The Security Rule, and the HITECH Act
- The Privacy Rule, applies to protected health information (PHI) in any form whether paper, oral, electronic, etc. While it requires covered entities to put in place “administrative, physical, and technical safeguards” for protecting PHI, it differs from the Security Rule in that it discusses the cases in which PHI can be used, when authorization is required and what are patients’ rights with respect to their health information. (Page 8335 of the final Security Rule)
Summary of Privacy Rule
- The Security Rule applies only to protected health information in electronic form (E-PHI) and builds on the Privacy Rule requirements of “administrative, physical, and technical safeguards.”Unlike the Privacy Rule which is more concerned about patients’ rights and how health information is used and released, the Security Rule sets standards on the processes and technical security measures that should be taken to keep PHI private.It discusses acceptable ways to “implement basic safeguards to protect E-PHI from unauthorized access, alteration, deletion, and transmission.” (Page 8335 of the final Security Rule)* Under the Security Rule, paper to-paper faxes, person-to-person telephone calls, video teleconferencing, or messages left on voice-mail do not count as E-PHI because they did not exist in electronic form before the transmission.Thus those activities are not covered by [the Security Rule]” (Page 8342 of the final Security Rule). In contrast, the Privacy Rule applies to all forms of PHI.In particular, it calls for attention to:
- risk analysis and management
- administrative, technical, and physical safeguards
- organizational requirements
- policies, procedures, and documentation requirementsSecurity Rule Guidance MaterialThe US Department of Health & Human Services (HHS) now also offers a Security Risk Assessment (SRA) tool to help organizations ensure they are compliant with HIPAA’s administrative, technical, and physical safeguards and to expose areas where their PHI may be at riskThe figure below gives you an idea of the security measures covered by the Security Rule. (from the paper “Reassessing Your Security Practices in a Health IT Environment: A Guide for Small Health Care Practices”)
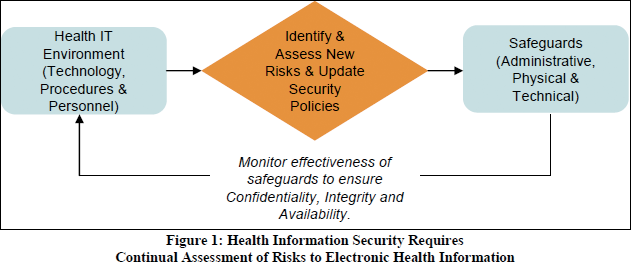
- The HITECH Act essentially added teeth to the HIPAA Privacy and Security Rules by specifying levels of violations and penalties for violations. It also requires periodic audits to ensure that covered entities and business associates are complying with the HIPAA Privacy and Security Rules and Breach Notification.
Who Is Required To Comply With HIPAA?
Not all operations that handle health-related information must follow HIPAA law (such as many schools, state agencies, law enforcement agencies, or municipal offices). Under HIPAA the 2 groups that must follow HIPAA rules are
- covered entities – health care providers, health plans, and health clearing houses
- business associates – a person or group providing certain functions or services for a covered entity which require access to identifiable health information, such as a CPA firm, an attorney, or an independent medical transcriptionist
More business associate FAQs here
Doctors By Video, LLC would be considered the business associate of a covered entity that uses Doctors By Video, LLC to communicating private health information with a client.
Is A Software Vendor Considered a Business Associate Under HIPAA?
It depends. If a vendor or subcontractor transmits, maintains, or has routine access to protected health information (PHI) when providing its services to a covered entity then it is considered a business associate. For example, a vendor that hosts the software containing patient information on its own server or accesses patient information when troubleshooting the software, then it is considered a business associate and must have a business associate agreement with the covered entity as specified under the HIPAA Privacy Rule 45 C.F.R. § 164.504(e).
The only exception under HITECH section 13408 is in the case of a data transmission organization that acts as a conduit, in that it only transports information but does not access it, such as the US Postal Service or its electronic equivalent — Internet Service Providers (ISPs), a telecommunication company, etc.
While these may have access to PHI, they only access PHI on a random or infrequent basis as necessary for the performance of the transportation service or as required by law: “[D]ata transmission organizations that do not require access to protected health information on a routine basis would not be treated as business associates” (p. 22)
While Doctors By Video, LLC never has access to any information, health or otherwise, that you may observe, transmit, or receive by using Doctors By Video, LLC, it is still considered a business associate because it is used to transmit private health information over the Internet. To be HIPAA-compliant, a covered entity using Doctors By Video, LLC for this purpose must have a Business Associate agreement with Doctors By Video, LLC.
U.S. Department of Health on Software Vendors
How is HIPAA involved in your use of video conferencing?
Videoconferencing may involve the electronic exchange of health information which is protected under HIPAA law. Security considerations with video conferencing may involve making sure unauthorized third parties cannot record or “listen in” on a video conferencing session, making sure recorded video conferencing sessions are stored and identified in a secure and proper manner, or having a procedure for initiating and receiving video calls. Other video collaboration features affecting security may include text chat, screen-sharing, and file transfer.
Videoconferencing would only be one small piece to consider when establishing and maintaining HIPAA-compliant IT security standards as described by the Privacy Rule and the Security Rule.
How does Doctors By Video, LLC allow you to comply with the HIPAA Privacy and Security Rules?
Doctors By Video, LLC has several characteristics that make it easy to protect the confidentiality of protected health information:
- Peer-to-Peer sessions
Doctors By Video, LLC uses a managed peer-to-peer architecture, where video (and other media) are streamed directly from endpoint to endpoint. Information is never stored on any Doctors By Video, LLC servers or intercepted by Doctors By Video, LLC in any way. The Doctors By Video, LLC management server is only used for address lookup, connection brokering, and system/user administration. This prevents information leakage between point A and point B.
- Encryption
Encryption adds another layer of security for our services. All Doctors By Video, LLC traffic is encrypted with FIPS 140-2 certified 256-bit Advanced Encryption Standard. Non of our servers have access to the decryption keys. This keeps your videoconference absolutely confidential.
- Local File Storage (of non-streaming media)
Doctors By Video, LLC will soon allows users to record video conferences and keep chat history that could be regarded as electronic protected health information (e-PHI). These files are stored on a user’s computer and are not accessible to Doctors By Video, LLC. Covered entities may securely save recorded conferences or chat histories to their own HIPAA compliant electronic health record (EHR) system.
Is Doctors By Video, LLC certified for use under HIPAA?
Certification of health technology is regulated under the HITECH Act by the Office of the National Coordinator for Health Information Technology (ONC) in collaboration with the National Institute of Standards and Technology (NIST). HIPAA rules do “not assume the task of certifying software and off-the-shelf products” (p. 8352 of the Final Security Rule) neither do they set criteria for or accredit independent agencies that do HIPAA certifications.
In short, this means that the third-party HIPAA certification groups you may use are not regulated by any federal accreditation agency.
Currently, HITECH only provides for the testing and certification of Electronic Health Records (EHR) programs and modules. The certification is generally used to qualify health operations for Medicare and Medicaid EHR Incentive Programs.
Doctors By Video, LLCis not an EHR software or module.
Does Doctors By Video, LLC Offer A HIPAA Business Associate Contract?
Doctors By Video, LLC signs HIPAA Business Associate Agreements with our clients.
U.S. Department of Health on Business Associate Agreements
Does data have to be encrypted to be HIPAA compliant?
The Security Rule does not require encryption if an entity can prove it is not reasonable or appropriate to do so. However, it is a good idea to encrypt data whenever possible because in the case that there is a data breach, proper encryption exempts HIPAA-covered entities from the Breach Rule (section 13402 of the HITECH Act), which requires notification of PHI that has not been secured (i.e. encrypted) according to the security guidance publication (74 FR 19006 on April 27, 2009):“While covered entities and business associates are not required to follow the guidance, the specified technologies and methodologies, if used, create the functional equivalent of a safe harbor, and thus, result in covered entities and business associates not being required to provide the notification otherwise required by section 13402 in the event of a breach.” (p. 19008)
Encryption processes that have been tested and meet the guidance standard:(i) “Valid encryption processes for data at rest are consistent with NIST Special Publication 800–111, Guide to Storage Encryption Technologies for End User Devices.” (p. 19009-10)(ii) “Valid encryption processes for data in motion are those that comply with the requirements of Federal Information Processing Standards (FIPS) 140–2. These include, as appropriate, standards described in NIST Special Publications 800–52, Guidelines for the Selection and Use of Transport Layer Security (TLS) Implementations; 800–77, Guide to IPsec VPNs; or 800–113, Guide to SSL VPNs, and may include others which are FIPS 140–2 validated.” (p. 19009-10)
Doctors By Video, LLC does not store any of your data. All Doctors By Video, LLC traffic is encrypted with FIPS 140-2 compliant 256-bit Advanced Encryption Standard.
Official Documentation For HIPAA
HIPAA – Health Insurance Portability and Accountability Act of 1996, Public Law 104-191, the complete suite of HIPAA Administrative Simplification Regulations can be found at 45 C.F.R.Part 160, Part 162, and Part 164
The Privacy Rule – “Standards for Privacy of Individually Identifiable Health Information” and is found at 45 CFR Part 160 and Subparts A and E of Part 164.
The Security Rule – “Security Standards for the Protection of Electronic Protected Health Information” and is found at 45 CFR Part 160 and Subparts A and C of Part 164.
Modifications to the HIPAA Privacy, Security, Enforcement, and Breach Notification Rules – 45 C.F.R. Parts 160 and 164
*ATTRIBUTES: VSEE.com | The US Department of Health & Human Services | © 2020 Doctors By Video LLC.
Digital Millennium Copyright Act Policy
Welcome to https://www.addameeting.com (the “Site”). We respect the intellectual property rights of others just as we expect others to respect our rights. Pursuant to Digital Millennium Copyright Act, Title 17, United States Code, Section 512(c), a copyright owner or their agent may submit a takedown notice to us via our DMCA Agent listed below. As an internet service provider, we are entitled to claim immunity from said infringement claims pursuant to the “safe harbor” provisions of the DMCA. To submit a good faith infringement claim to us, you must submit the notice to us that sets forth the following information:
Notice of Infringement – Claim
- A physical or electronic signature of the copyright owner (or someone authorized to act on behalf of the owner);
- Identification of the copyrighted work claimed to have been infringed;
- Identification of the infringing material to be removed, and information reasonably sufficient to permit the service provider to locate the material. [Please submit the URL of the page in question to assist us in identifying the allegedly offending work];
- Information reasonably sufficient to permit the service provider to contact the complaining party including your name, physical address, email address, phone number and fax number;
- A statement that the complaining party has a good faith belief that the use of the material is unauthorized by the copyright agent; and
- A statement that the information in the notification is accurate, and, under penalty of perjury, that the complaining party is authorized to act on behalf of the copyright owner.
Title 17 USC §512(f) provides civil damage penalties, including costs and attorney fees, against any person who knowingly and materially misrepresents certain information in a notification of infringement under 17 USC §512(c)(3).
Send all takedown notices through our Contact page. Please send by email for prompt attention.
Please note that we may share the identity and information in any copyright infringement claim we receive with the alleged infringer. In submitting a claim, you understand accept and agree that your identity and claim may be communicated to the alleged infringer.
Counter Notification – Restoration of Material
If you have received a notice of material being takedown because of a copyright infringement claim, you may provide us with a counter notification in an effort to have the material in question restored to the site. Said notification must be given in writing to our DMCA Agent and must contain substantially the following elements pursuant to 17 USC Section 512(g)(3):
- Your physical or electronic signature.
- A description of the material that has been taken down and the original location of the material before it was taken down.
- A statement under penalty of perjury that you have a good faith belief that the material was removed or disabled as a result of mistake or misidentification of the material to be removed or disabled.
- Your name, address, and telephone number, and a statement that you consent to the jurisdiction of the federal district court for the judicial district in which the address is located (or if you are outside of the United States, that you consent to jurisdiction of any judicial district in which the service provider may be found), and that you will accept service of process from the person or company who provided the original infringement notification.
- Send your counter notice through our Contact page. Email is highly recommended.
Repeat Infringer Policy
We take copyright infringement very seriously. Pursuant to the repeat infringer policy requirements of the Digital Millennium Copyright Act, we maintain a list of DMCA notices from copyright holders and make a good faith effort to identify any repeat infringers. Those that violate our internal repeat infringer policy will have their accounts terminated.
Modifications
We reserve the right to modify the contents of this page and its policy for handling DMCA claims at any time for any reason. You are encouraged to check back to review this policy frequently for any changes.
Privacy Notice For California Residents
Definitions
Website
Doctors By Video, LLC. / https://www.telehealthy.us / https://addameeting.com
Owner (or We)
Indicates the natural person(s) or legal entity that provides this Website to Users.
User (or You)
Indicates any natural person or legal entity using this Website.
This Privacy Notice for California Residents supplements the information contained in the Website’s Privacy Policy and applies solely to all visitors, users, and others who reside in the State of California. We adopted this notice to comply with the California Consumer Privacy Act of 2018 (CCPA) and any terms defined in the CCPA have the same meaning when used in this notice.
Information We Collect
The Website collects information that identifies, relates to, describes, references, is capable of being associated with, or could reasonably be linked, directly or indirectly, with a particular consumer or device (“personal information”).
In particular, Website has collected the following categories of personal information from its consumers within the last 12 months:
| Category | Examples | Collected |
|---|---|---|
| A. Identifiers. | A real name, alias, postal address, unique personal identifier, online identifier, Internet Protocol address, email address, account name, Social Security number, driver’s license number, passport number, or other similar identifiers. | YES |
| B. Personal information categories listed in the California Customer Records statute (Cal. Civ. Code § 1798.80(e)). | A name, signature, Social Security number, physical characteristics or description, address, telephone number, passport number, driver’s license or state identification card number, insurance policy number, education, employment, employment history, bank account number, credit card number, debit card number, or any other financial information, medical information, or health insurance information. | YES |
| C. Protected classification characteristics under California or federal law. | Age (40 years or older), race, color, ancestry, national origin, citizenship, religion or creed, marital status, medical condition, physical or mental disability, sex (including gender, gender identity, gender expression, pregnancy or childbirth and related medical conditions), sexual orientation, veteran or military status, genetic information (including familial genetic information). | YES |
| D. Commercial information. | Records of personal property, products or services purchased, obtained, or considered, or other purchasing or consuming histories or tendencies. | YES |
| E. Biometric information. | Genetic, physiological, behavioral, and biological characteristics, or activity patterns used to extract a template or other identifier or identifying information, such as fingerprints, faceprints, and voiceprints, iris or retina scans, keystroke, gait, or other physical patterns, and sleep, health, or exercise data. | YES |
| F. Internet or other similar network activity. | Browsing history, search history, information on a consumer’s interaction with a Website, application, or advertisement. | YES |
| G. Geolocation data. | Physical location or movements. | YES |
| H. Sensory data. | Audio, electronic, visual, thermal, olfactory, or similar information. | YES |
| I. Professional or employment-related information. | Current or past job history or performance evaluations. | YES |
| J. Non-public education information (per the Family Educational Rights and Privacy Act (20 U.S.C. Section 1232g, 34 C.F.R. Part 99)). | Education records directly related to a student maintained by an educational institution or party acting on its behalf, such as grades, transcripts, class lists, student schedules, student identification codes, student financial information, or student disciplinary records. | YES |
| K. Inferences drawn from other personal information. | Profile reflecting a person’s preferences, characteristics, psychological trends, predispositions, behavior, attitudes, intelligence, abilities, and aptitudes. | YES |
Personal information does not include:
- Publicly available information from government records.
- Deidentified or aggregated consumer information.
- Information excluded from the CCPA’s scope, like certain health or medical information and other categories of information protected by different laws.
We obtain the categories of personal information listed above from the following categories of sources:
- Directly from you. For example, from forms you complete or products and services you purchase.
- Indirectly from you. For example, from observing your actions on our Website.
Use of Personal Information
We may use or disclose the personal information we collect for one or more of the following business purposes:
- To fulfill or meet the reason you provided the information. For example, if you share your name and contact information to request a price quote or ask a question about our services, we will use that personal information to respond to your inquiry. If you provide your personal information to purchase a product or service, we will use that information to process your payment and facilitate delivery. We may also save your information to facilitate new product orders or process returns.
- To process your requests, purchases, transactions, and payments and prevent transactional fraud.
- To provide you with support and to respond to your inquiries, including to investigate and address your concerns and monitor and improve our responses.
- To respond to law enforcement requests and as required by applicable law, court order, or governmental regulations.
- As described to you when collecting your personal information or as otherwise set forth in the CCPA.
- To evaluate or conduct a merger, divestiture, restructuring, reorganization, dissolution, or other sale or transfer of some or all of our or our affiliates’ assets in which personal information held by us or our affiliates about our Website users is among the assets transferred.
We will not collect additional categories of personal information or use the personal information we collect for materially different, unrelated, or incompatible purposes without providing you notice.
Sharing Personal Information
We may disclose your personal information to a third party for a business purpose. When we disclose personal information for a business purpose, we enter a contract that describes the purpose and requires the recipient to both keep that personal information confidential and not use it for any purpose except performing the contract.
We share your personal information with the following categories of third parties:
- Service providers.
- Data Aggregators.
Your Rights and Choices
The CCPA provides consumers (California residents) with specific rights regarding their personal information. This section describes your CCPA rights and explains how to exercise those rights.
Access to Specific Information and Data Portability Rights
You have the right to request that we disclose certain information to you about our collection and use of your personal information over the past 12 months. Once we receive and confirm your verifiable consumer request (see Exercising Access, Data Portability, and Deletion Rights), we will disclose to you:
- The categories of personal information we’ve collected about you.
- The categories of sources for the personal information we’ve collected about you.
- Our business or commercial purpose for collecting or selling that personal information.
- The categories of third parties with whom we share that personal information.
- The specific pieces of personal information we’ve collected about you (also called a data portability request).
- If we sold or disclosed your personal information for a business purpose, two separate lists disclosing:
- sales, identifying the personal information categories that each category of recipient purchased; and
- disclosures for a business purpose, identifying the personal information categories that each category of recipient obtained.
Deletion Request Rights
You have the right to request that we delete any of your personal information that we collected from you and retained, subject to certain exceptions. Once we receive and confirm your verifiable consumer request (see Exercising Access, Data Portability, and Deletion Rights), we will delete (and direct our service providers to delete) your personal information from our records, unless an exception applies.
We may deny your deletion request if retaining the information is necessary for us or our service provider(s) to:
- Complete the transaction for which we collected the personal information, provide a good or service that you requested, take actions reasonably anticipated within the context of our ongoing business relationship with you, or otherwise perform our contract with you.
- Detect security incidents, protect against malicious, deceptive, fraudulent, or illegal activity, or prosecute those responsible for such activities.
- Debug products to identify and repair errors that impair existing intended functionality.
- Comply with the California Electronic Communications Privacy Act (Cal. Penal Code § 1546 seq.). Enable solely internal uses that are reasonably aligned with consumer expectations based on your relationship with us.
- Comply with a legal obligation.
- Make other internal and lawful uses of that information that are compatible with the context in which you provided it.
Exercising Access, Data Portability, and Deletion Rights
To exercise the access, data portability, and deletion rights described above, please submit a verifiable consumer request to us by either:
- Calling us at 4433713181
- Emailing us at [email protected]
Only you, or a person registered with the California Secretary of State that you authorize to act on your behalf, may make a verifiable consumer request related to your personal information. You may also make a verifiable consumer request on behalf of your minor child.
You may only make a verifiable consumer request for access or data portability twice within a 12-month period. The verifiable consumer request must:
- Provide sufficient information that allows us to reasonably verify you are the person about whom we’ve collected personal information or an authorized representative.
- Describe your request with sufficient detail that allows us to properly understand, evaluate, and respond to it.
We cannot respond to your request or provide you with personal information if we cannot verify your identity or authority to make the request and confirm the personal information relates to you.
Making a verifiable consumer request does not require you to create an account with us.
We will only use personal information provided in a verifiable consumer request to verify the requestor’s identity or authority to make the request.
Response Timing and Format
We endeavor to respond to a verifiable consumer request within forty-five (45) days of its receipt. If we require more time, we will inform you of the reason and extension period in writing.
We will deliver our written response by mail or electronically, at your option.
Any disclosures we provide will only cover the 12-month period preceding the verifiable consumer request’s receipt. The response we provide will also explain the reasons we cannot comply with a request, if applicable. For data portability requests, we will select a format to provide your personal information that is readily useable and should allow you to transmit the information from one entity to another entity without hindrance.
We do not charge a fee to process or respond to your verifiable consumer request unless it is excessive, repetitive, or manifestly unfounded. If we determine that the request warrants a fee, we will tell you why we made that decision and provide you with a cost estimate before completing your request.
Personal Information Sales
We will not sell your personal information to any party. If in the future, we anticipate selling your personal information to any party, we will provide you with the opt-out and opt-in rights required by the CCPA.
Non-Discrimination
We will not discriminate against you for exercising any of your CCPA rights. Unless permitted by the CCPA, we will not:
- Deny you goods or services.
- Charge you different prices or rates for goods or services, including through granting discounts or other benefits, or imposing penalties.
- Provide you a different level or quality of goods or services.
- Suggest that you may receive a different price or rate for goods or services or a different level or quality of goods or services.
Other California Privacy Rights
California’s “Shine the Light” law (Civil Code Section § 1798.83) permits users of our Website that are California residents to request certain information regarding our disclosure of personal information to third parties for their direct marketing purposes. To make such a request, please send an email to [email protected].
Changes to Our Privacy Notice
We reserve the right to amend this privacy notice at our discretion and at any time. When we make changes to this privacy notice, we will post the updated notice on our Website and update the notice’s effective date. Your continued use of our Website following the posting of changes constitutes your acceptance of such changes.
Contact Information
If you have any questions or comments about this notice, the ways in which we collect and use your information described below and in our Privacy Policy, your choices and rights regarding such use, or wish to exercise your rights under California law, please do not hesitate to contact us at:
Contact ADDaMeeting.com
Text & Phone: 443.371.3181
Email: [email protected]
Business Hours: Always Open
- About Us | Pricing | Privacy Policy | Term of Use -